SecureID RSA Authentication stands as a pivotal solution in the realm of system security. Its role is to authenticate users accessing systems and applications, especially those hosted on Linux platforms. By leveraging RSA’s robust cryptographic algorithms, it ensures that access to networked services and applications is tightly controlled and secure.
Evolution of SecureID RSA
The evolution of SecureID RSA can be traced from its origins as a straightforward token-based mechanism to its current status as a sophisticated, multi-factor authentication system. The key to its widespread adoption in Linux environments has been its adaptability and the increasing need for more secure authentication methods in response to evolving cyber threats.
Installation Procedure for SecureID RSA on Linux
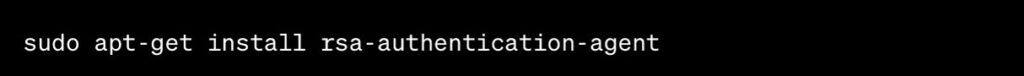
For programmers looking to deploy SecureID RSA on a Linux system, the initial step involves installing the necessary software components. This process is initiated with the command:
Integration Process with Linux Systems
The integration of SecureID RSA with Linux is not a trivial task and requires meticulous configuration. It necessitates editing specific system configuration files and properly setting up RSA modules to ensure seamless communication with RSA authentication servers. This step is critical for the effective functioning of the authentication process.
Application Scenarios: SecureID RSA in Linux Environments
SecureID RSA’s adaptability makes it a vital tool in Linux environments, addressing a range of security needs:
Remote Server Access
In the context of remote server access, SecureID RSA plays a critical role. Its implementation ensures that access to remote servers is gated behind robust authentication, allowing only verified users to connect. This is particularly relevant for organizations managing sensitive data over remote networks.
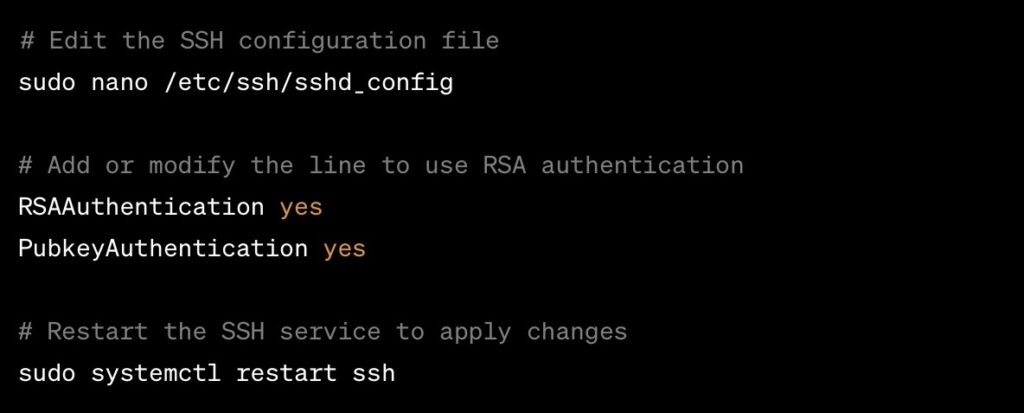
Implementing SecureID RSA for SSH Connections
SecureID RSA is integral to securing SSH (Secure Shell) connections. SSH, a protocol for secure network services, is heavily relied upon for safe remote operations, including logins and file transfers. Here’s a basic implementation snippet for integrating SecureID RSA with SSH on Linux:
Industry-Specific Applications
SecureID RSA’s application extends across various sectors, each with unique security needs:
- Banking and Finance: It safeguards financial transactions and sensitive customer data against unauthorized access;
- Healthcare: In healthcare, SecureID RSA is used to maintain the confidentiality and integrity of patient records and medical information;
- Government Agencies: SecureID RSA is employed to protect state and federal systems, ensuring the security of governmental data and communications.
Performance Optimization Strategies
To maximize SecureID RSA’s effectiveness on Linux systems, consider the following strategies:
Regular Software Updates
Keeping both the RSA software and the Linux operating system up-to-date is crucial. This practice not only ensures compatibility but also guards against vulnerabilities that emerge over time. Scheduled updates can be managed through Linux’s package management systems like apt or yum.
System Compatibility Checks
Ensuring that the hardware and software environments are conducive to SecureID RSA’s optimal performance is vital. This involves verifying that the Linux distribution in use is compatible with the SecureID RSA version and checking for any hardware requirements or limitations.
Fine-Tuning RSA Settings
Customizing RSA settings to align with specific security requirements and use cases is essential. This may involve adjusting timeout settings, configuring user access policies, or setting up specific cryptographic protocols.
Addressing Challenges and Solutions in Implementation
Navigating Implementation Complexities
Implementing SecureID RSA on Linux can present unique challenges:
- System Compatibility Issues: Ascertain that SecureID RSA is compatible across various Linux distributions, paying attention to specific version requirements or dependencies;
- Configuration Complexities: The correct configuration of SecureID RSA is key. This involves setting up the RSA module to communicate effectively with RSA servers, which requires a deep understanding of both the Linux system and the RSA technology.
Troubleshooting Common Problems
Configuration Errors
Mistakes in configuring SecureID RSA can lead to functional issues. These might include incorrect file permissions, errors in configuration files, or misaligned system settings. Regular audits and reviews of configuration files are recommended to prevent and address these issues.
Connectivity Issues
Challenges in network connectivity can disrupt communication with RSA servers, hindering the authentication process. This requires consistent monitoring of network performance and thorough log analysis to identify and resolve connectivity problems promptly.
Prospects of SecureID RSA and Linux
The trajectory of SecureID RSA in the context of Linux systems points towards integration with emerging technologies and adaptation to new security challenges. Programmers must stay abreast of developments in fields like artificial intelligence, machine learning, and quantum computing, which are poised to influence future iterations of security protocols.
Monitoring Disk Space for SecureID RSA on Linux
Importance of Disk Space Management in SecureID RSA Deployment
Effective disk space management is crucial when deploying SecureID RSA on Linux systems. Adequate disk space ensures that the RSA system functions optimally without interruptions due to storage constraints. This is especially important for maintaining logs, temporary files, and the RSA database, which are essential for security audits and troubleshooting.
How to Check Disk Space in Linux
Using the df Command
The df (disk free) command is a standard tool in Linux for monitoring disk space usage. It provides a quick overview of the available and used space on all mounted filesystems. To use the df command, open the terminal and input:

The -h option displays the output in a human-readable format, showing sizes in KB, MB, or GB as appropriate. This command helps in identifying if the disk space is sufficient for SecureID RSA operations.
Analyzing Specific Directories
For a more detailed analysis, especially focusing on directories relevant to SecureID RSA, the du (disk usage) command can be used. This command is beneficial for monitoring the size of specific directories, such as log directories. To check the disk usage of a particular directory, use:

This command provides the total size of the specified directory. Replacing /path/to/directory with the actual path of the RSA-related directories allows administrators to monitor their sizes and manage space accordingly.
Integrating Disk Space Monitoring with SecureID RSA Maintenance
In the context of SecureID RSA on Linux, regularly checking disk space is a part of proactive system maintenance. It ensures that there is enough space for the RSA system to store its necessary data and operate effectively. Automated scripts or system monitoring tools can be configured to alert administrators when disk space falls below a certain threshold, allowing for timely interventions to prevent system disruptions.
Conclusion
In summary, SecureID RSA Authentication on Linux is an indispensable tool for programmers focused on securing systems and data. Mastery of RSA algorithms and a deep understanding of Linux systems are essential for effective implementation and maintenance. This knowledge not only enhances system security but also prepares programmers for future advancements in the field of cybersecurity authentication.
